TLS/SSL for Microgaming Casinos – Architecture and Processes
Microgaming websites have a reputation of well-secured gambling entertainments because this company implements necessary standards, strong firewalls and modern encryption technologies in all of its products.
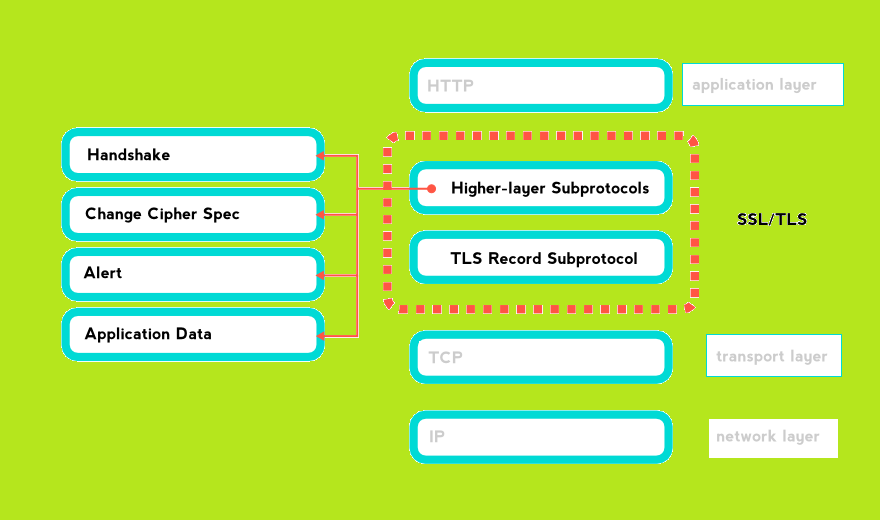
The defense of sent/received information (for example credit card numbers) is maintained using TLS/SSL in Microgaming casinos. It has a structure of two main parts. One sector is built mainly with Handshake Protocol (contains several separate elements) and application one. Another sector is the Record Protocol.
Exploiting such protection techniques is possible with launching such processes as selecting the cipher suite (to establish negotiations), authentication, key exchange (for transforming info into encrypted data) and sharing of the application information.
TLS or SSL?
Actually, there are some important differences that should be considered when deciding to use one of them. Despite they share a common purpose (to protect data by establishing secure sender/receiver communication), the question which one offers better defense is relevant nowadays.
The principal distinction is that SSL occurs to use an explicit connection to the server (i.e. by port). That means that “conversation” begins on already secured channels. So when using TLS, different ports perform their greetings at first, and in case the “handshake” is successful, then further communication will be switched to a safe level. SSL, being a much earlier technology, proves to be not so efficient nowadays due to the development of various hacking methods.
However, TLS (especially types v1.0 and 1.2) is the latest tool which is able to fence off sensitive info from unauthorized access. That’s why it is a priority to deal only with the new inventions.
TLS Record Protocol
It provides a defense for the app info with an assistance of the keys generated after Handshake. The responsibility of this tool is confirming the non-interference and safety of application data and its sources.
Process
The RP extracts the info packages from the app layer, ciphers it and later routes to the TL (Transport Layer).
So, when it receives data, it starts the fragmenting process to comply with the required length of the algorithm and launches compressing/decompressing. Then a computing operation goes with the help of the information received from the Handshake Protocol. The outcome is transferred to the TL.
Encryption
The ciphering types (for the RP) can change during the settlement of the configurations. So various encryption methods will be switched at different phases of the process.
Public Key
This encryption method works this way:
The RP starts hashing outgoing information, then the outcome will be encrypted using the Pr key of the sender. And the entering data will be deciphered with the Pb one.
Symmetric Key
The SK ciphering includes creating the shared session key. So when the Handshake process is ending, the protocol swaps the data between the customer and the server for launching an operation of computing various types of keys.
When the set of generating chain numbers is available, the server and the client deliver a report to Change Cipher Spec. And thus, at this stage, they terminate their work with previously used keys (public-private), but start working with the shared session one.
Without Encryption
There might be a case when no encryption is used at all. If there is no compromising on what cipher suite and security channel to choose, the state will be indicated as Null. Also, the operations of authentication and calculating won’t be performed.
TLS Handshake Protocols on Microgaming Casino Websites
Firstly, such technology (layer) on Microgaming rooms has a purpose of selecting a cipher suite and algorithms of compression.
Secondly, it maintains the authentication procedure. That is confirming a period of validity, digital signature, and other parameters to verify the identification.
Thirdly, this protocol is responsible for sharing random digits for starting the encryption procedure.
And finally, while the handshake procedure is in progress, the hashing will begin. This process is crucial, as it allows substituting the bigger quantity of data with the smaller representatives for successful transportation of integrated information. After this, the outcome will play a role of digital fingerprints.
Besides, there are several sub-types, described below.
Alert
The first one is called Alert. It serves for announcing to the peer about an alteration in states or some errors. Actually, there are various alerts that can warn about any changes or mistakes. They are usually sent because of terminated connection, wrong message or in the case decryption of the received notice is impossible.
Handshake
Such sub-type has a goal of setting session information. This info includes an ID, the kind of cipher to work with, type of compression algorithm, certificates and etc.
Change Cipher Spec
It is responsible for altering the ciphering within a recipient-sender connection. The keying chain will be changed by simply requesting a peer to start switching (using this protocol). Thus, a renewed set of keys will be generated for further usage.
Encryption
Nowadays, ciphering uses two kinds of keys. These are symmetric and asymmetric ones. TLS/SSL exploits both of them for various encryption processes. We will describe each one further.
Private Key
The tool is also called the SK, as it allows ciphering/deciphering info with the assistance of the same key chain. By the way, such method is ideal for operating with huge quantities of information because it takes less time for computing.
Public Key
Such method implies generating two different keys. One will be held secretly, while another might come along with certification. So to start ciphering/deciphering two different number sets are needed.
In TLS/SSL technology, asymmetric keys are necessary for authenticating the server to the customer and vice versa.