This substantial presentation is designed to introduce the novice to the concepts and principles of cryptography, and give a sound platform from which to contribute to any implementation project or discussion. It is targeted at any group anxious to learn about the topic, but is particularly suited to executive management, and includes comprehensive speaker notes. The following samples help to illustrate the depth and quality of this:
Typical Foils:
Cryptography Basics
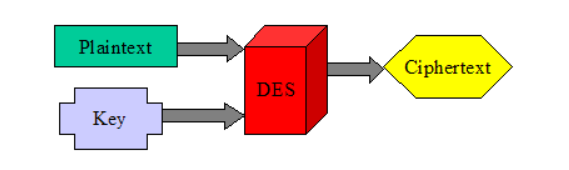
- DES (Data Encryption Standard)
— Block size is 64 bits
— Key size is 56 bits
— Most widely used block cipher in the world
- One bit change in either the key or the plaintext should cause about 50%
change in the cipher text. - Key size has always been criticized as possibly being too short and may be
vulnerable to exhaustive search. - 1,000,000 processors each testing 1,000,000 keys per second could try all
possible keys in about 24 hours. - If not considered sufficiently secure use triple-DES with 112-bit or 168-bit
keys.
Cryptography Basics
Digital Signature
- — Hash the message to be signed.
- — Pad the result out to the length of the modulus as suggested on the previous slide.
- — Encrypt the result with your private key.
- — The encrypted block is the digital signature.
- — Send the digital signature along with the message.
- — The receiver verifies the signature with your public key.
Cryptography Basics
Certification Authority
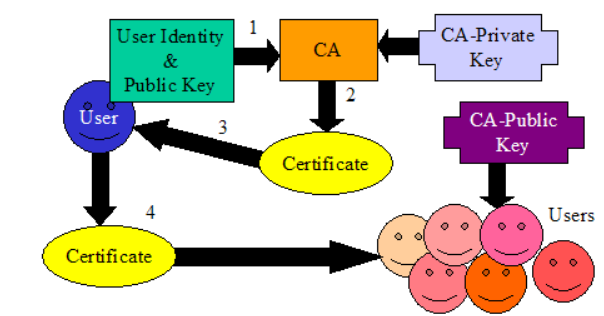
- Because of the critical nature of the CA, maximum security is required.
- Expect a CA key to be considerably longer than auser key (not a mathematical requirement, because you can sign along key with a short one — merely common sense!)
- Notice that once a certificate has been issued, it is up to the user (not the CA) how and to whom it gets distributed. It might be that the user simply sends his certificate to the owner of an online directory.
Cryptography Basics
Hash Algorithms
- — When creating a digital signature you hash your message down to a manageable size so that it will fit into the block to be encrypted with your private key.
- — The two most common hash algorithms are MDS (gives a 16-byte digest) and SHA-1 (a 20-byte digest).
- — The two algorithms are very similar in form, but SHA-1 is preferred because the longer digest reduces the probability of collisions (two messages having the same digest).
- MDS5 was invented by Ronald Rivest. Message Digest 5 (there were earlier versions which did not gain wide acceptance).
- SHA-1 is a modification of an earlier algorithm (Secure Hash Algorithm). Source of the algorithm is National Institute of Standards (NIST).
- The properties required of a good hash algorithm are:
- eEasy and quick to reduce a message of any size to afixedlength digest.
- Computationally infeasible to construct a meaningful message from a given digest.
- Very low probability that two different messages will yield the same digest.
PURCHASE PAGE
The Cryptography Management Kit can now be purchased online and downloaded directly to your PC. It couldn’t be easier.
To purchase the product and download for a special price of just $199, simply visit our Crypto Purchase Page.



